How to Manage Crypto Keys Without Losing Sleep
If your crypto keys live on a laptop that touches the internet, you might as well assume they’re already compromised.
That sounds dramatic, but it’s true. Keys are everything in Web3. Lose them, leak them, or reuse them in the wrong place, and poof, your funds (or your company’s) are gone. No “forgot password” button here.
It’s also extremely hard to keep your system malware-free 100% of the time.
So how do you stay sane without turning into a paranoid hermit? By having a system. Here’s the one we recommend.
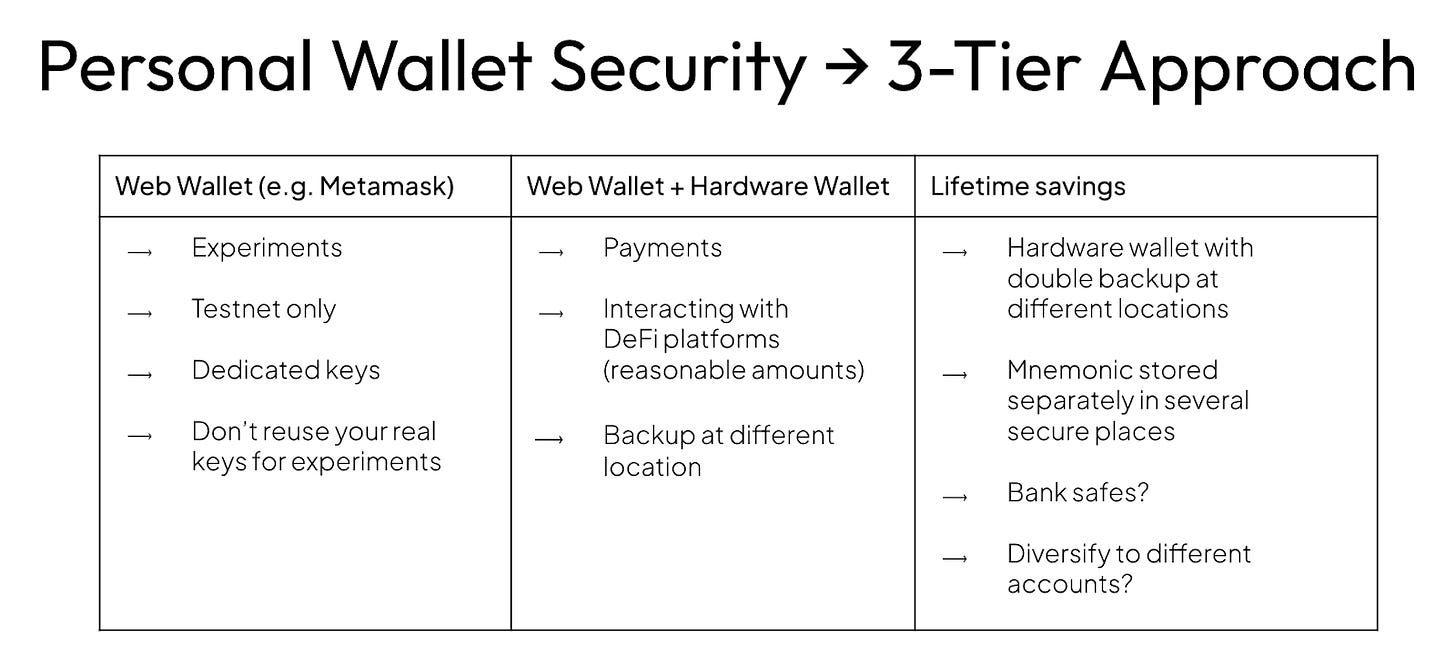
Step 1: Your Personal Wallets
Think of wallets like bank accounts. You don’t keep your life savings in your Venmo, right? Same logic here. Everyone’s circumstances are different, but here are our recommendations for the average crypto user:
Tier 1 - Web Wallet (Metamask, Rabby, etc.)
This is your “play money.” Use it for testnets, experiments, or just trying stuff out. Keep balances tiny. And please don’t reuse your real keys here.
Tier 2 - Web Wallet + Hardware Wallet
This one’s for day-to-day crypto life: paying people, interacting with DeFi platforms, moving “reasonable” amounts. Always use a hardware wallet. Keep backups somewhere safe, and not all in one place.
Tier 3 - Lifetime savings
This is where your real money lives. Hardware wallet, backed up twice, with recovery phrases stored in separate secure locations. Think bank safes or even diversify to different accounts. This is your “retire one day” stash.
Step 2: Team / Company Keys
Now, if you’re running a company or protocol, things get more serious. One sloppy shortcut can sink you.
Keep test/dev/admin/deployment keys strictly separate.
Use clean, dedicated machines for important signatures like upgrades or big transfers.
Only give access to people who truly need it. “Least privilege” isn’t just a buzzword.
Use a multisignature wallet whenever possible. .
Step 3: Multisig Without the Headaches
Multisig is powerful, but easy to get wrong.
Pick something well-tested, audited and user-friendly.
Use an odd threshold so you don’t get deadlocked.
Spread out your signers; different people, departments, even geographies.
Use dedicated hardware wallets for signing.
Rotate keys every so often.
And never just blind-sign transactions you don’t understand.
Pro tip: Transaction simulators like Tenderly are your friend. For very sensitive wallets keep the UI simple, and maybe even consider using a frozen self-hosted UI that you fully control.
Step 4: Custodying Customer Keys
Thinking of holding customer keys? Highly discouraged!. But if you absolutely must:
Use Hardware Security Modules (HSM).
Isolate signing software in Trusted Execution Environments (TEE)
Monitor and log everything.
Stick to the principle of least privilege.
But again, if you can avoid custody, avoid custody.
Step 5: Other Keys You’re Forgetting
It’s not just wallet keys that matter. Your team probably also has:
API keys
SSH keys
GitHub tokens
Certificates
Passkeys
MFA backup codes
These can get you hacked just as fast. Keep them in password managers, rotate them regularly, and never, ever commit them into repos or Slack messages.
Step 6: Rotate Keys Before They Rot You
Here’s a simple rule: if in doubt, swap it out. Some keys can live longer, some need short lifespans, but none should be eternal. Track them, rotate them, and revoke what you don’t need.
Step 7: Special Note for Developers
GitHub is a graveyard of leaked keys. Don’t add to it.
PATs (Personal Access Tokens) → store securely, time-limited, least privilege.
SSH keys → harder to take shortcuts, always encrypt with a strong passphrase.
Never push secrets into repos. Not in .env, not in comments, not anywhere.
The Gold Standard (AKA: The Grown-Up Way)
If you want a simple checklist, it’s this:
Keep keys as air-gapped as you can.
Use secure enclaves.
Don’t reuse keys.
Rotate keys regularly.
Use throwaway keys for dev/test.
Track and revoke keys properly.
That’s it. Not paranoia, just hygiene.
Key management sounds boring until you lose a few million. Then it’s all you think about.
Build the right habits now, and you’ll never have to explain to your investors, community, or yourself why your project lost funds to a dumb mistake.
Want to go deeper? We’re running two OpSec seminars in October:
45-minute crash course (for non-technical team members) → Oct 2, 4pm CET
2.5-hour deep dive (for Web3 teams) → Oct 7, 3pm CET
Sign up here to receive the streaming link and updates!
Since 2017, Oak Security has helped secure over 600 projects! not just through audits, but through training, OpSec, and hands-on support. Because secure code is only half the story.
Follow us on Twitter, book a slot, or request an audit on our website.